HackTheBox - Blunder Writeup
Initial Scan & FTP
I started with a fast nmap scan:
nmap -A -T4 -oN initial_scan.txt 10.10.10.191
Which returned this information:
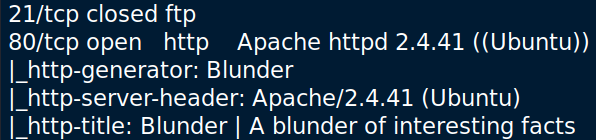
Afterward, I ran a scan of all TCP ports, but it didn’t provide new information.
I tried to contact with the ftp service in several ways, which is quite stupid in retrospect as the scan shows it is closed.
Poking Around the Website
I connected to the website and started looking around while gobuster was running:
gobuster dir -u 10.10.10.191 -w /usr/share/wordlists/dirb/big.txt -o big_root_gobust.txt -x txt,php,html
The scan revealed two interesting pages. The first is /todo.txt:
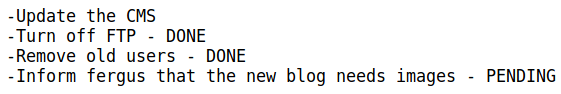
This gives us the notion the exploit has something to do with the CMS version and maybe images.
The second interesting page is the CMS admin login page, /admin.
Before we go any further let’s find out the CMS version. A peek at the source code reveals this:

The version is added as a request parameter to the resource GET requests probably for caching reasons.
Bruteforcing the CMS Login
This CMS version has three recorded CVEs, two of them are relevant to us. The first is an authentication brute-force mitigation bypass. We should be locked out after 10 login attempts, but we can spoof our address easily and pass that limit. More details here.
At first, the exploit didn’t work for me. Removing the WebAgent class fixed it.
- A quick google search showed that admin is the default username in Bludit, so I used it with rockyou.txt.
- Then I decided to change the username to fergus. It’s the guy from the note we found before.
- When that didn’t work I generated a wordlist using CeWL. It worked without any modification.
Gaining Access
Now that I have the CMS creds I can use the second CVE with a Metasploit module. It uploads an image with a malicious payload and uses a crafted .htaccess file to bypass the file extension check and execute the code.
Privesc to Hugo
Printing /etc/passwd shows two interesting users, Hugo and Shaun. To read the user.txt file I need to become Hugo, so he is the target.
I looked in several places on the serves, including the long-awaited /ftp:
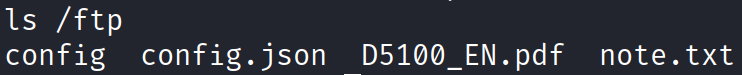
The file note.txt contains this:
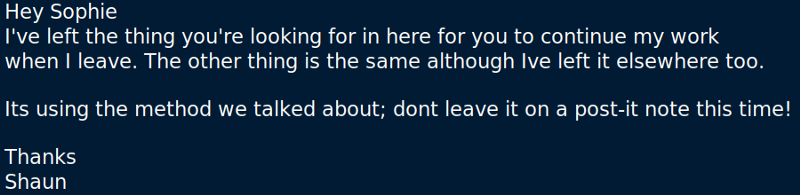
I tried looking for another occurrence of the files in the /ftp directory and failed. I even tried some stego on these poor files.
The rescue came with linPEAS which brought my attention to this file:
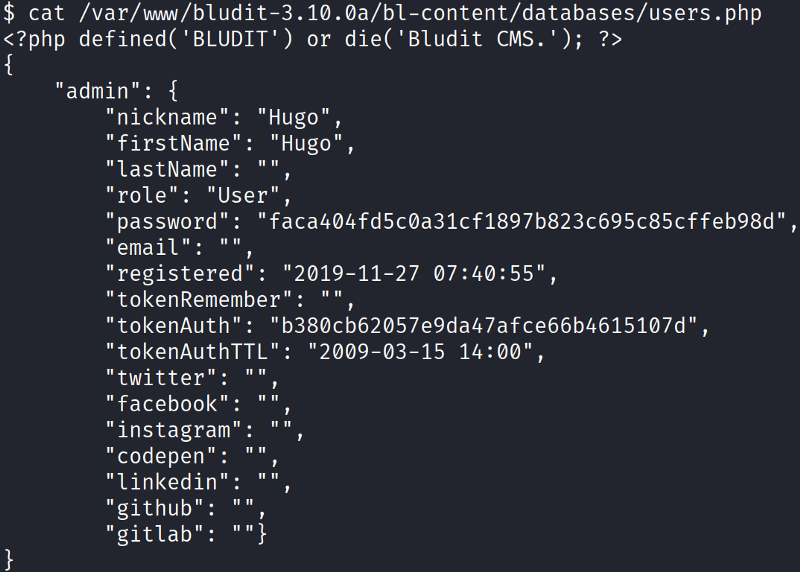
For some reason, there is a copy of the website with a newer CMS version, but this time the user recorded is Hugo and not Fergus. Hugo’s mistake was to use the same password for the CMS and the server. I used crackstation to crack the password hash and switched to Hugo with su.
Privesc to Root
To run sudo -l and a bunch of other reasons I need to have a TTY. To do so I need to create a reverse shell and upgrade it. I used the netcat one-liner and upgraded with python, you can find the commands here.
Sudo -l reveals this:
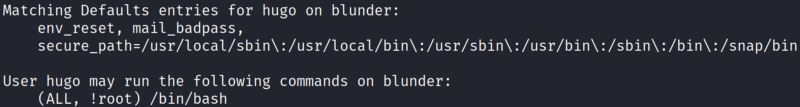
I can execute bash as whoever I want unless it’s root.
At this point, I made a mistake and switched to Shaun. He had some interesting properties, like being part of the lxd group. After some messing around I decided to try and look at Hugo’s sudo priveledges from a new perspective. I found out this vulnerability for sudo up to version 1.8.27. Armed with this weapon a simple command made me root:
sudo -u#-1 /bin/bash
Cheers!